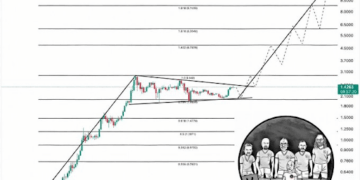
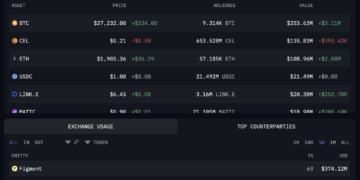
However, in interviews with CoinDesk, a pair of developers say that AJ’s depiction of the events is highly unlikely, if not impossible, and that standard operational security – such as double-checking that emails are from the proper sources and using a hardware wallet – is the best way forward.
Credit: Source link