Transaction batching protocol Furucombo has just lost $14 million in another “evil contract attack,” according to a recent report.
The tool enables users to “batch transactions using different decentralized Finance (DeFi) protocols at the same time.
About $14 million worth of different cryptocurrencies was transferred to the crypto address of the attacker from the platform. However, the amount seems to be higher than this since the attackers have been shifting Ethereaum (ETH) in batches to Tornado Cash over the past three hours.
Evil contract attack steadily on the rise
This type of attack on protocols seems to be growing in popularity and impact. Within a few months, users have lost over $70 million through this type of exploit on various protocols.
In an “evil contract exploit,” the threat actor opens a contract that deceives the protocol into recognizing it as belonging there, which opens up access to funds from the protocol.
The Furucombo hacking incident is similar to the last year’s “evil spell” attack on Struck Pickle Finance, which cost the platform about $20 million.
It’s also similar in concept to the $37 million “evil spell” attack on Alpha Francis earlier this month.
For the Furucombo attack, the threat actor made the protocol assume that their contract was the latest version of Aave. However, the attackers didn’t drain funds directly from the protocol, just like it happens with every evil contract exploit.
Instead, the attacker took advantage of the permissions given by users of the protocol to transfer funds. As protocols of this nature work, users may give token permissions on the protocol. So, the threat actors leveraged this opportunity to send funds from the accounts directly to their addresses.
Emiliano Bonassi, white-hat hacker and co-founder of DeFi Italy explained how the protocol works. “Infinite permissions means you can wipe everyone who interacted with Furucombo,” he said.
Many users have revoked their permissions
The Furucombo protocol team has released a statement regarding the attack. The team stated that the exploit has been mitigated, but it’s important not to throw caution to the wind. They have recommended the revoke of permissions for precautionary reasons. The team has also asked users to use the features at revoke cash to revoke permissions.
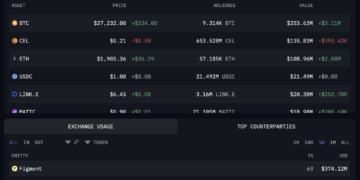
From the address of the attackers, it appears that most of the funds are no longer in the hackers’ address. As of the time of writing, the address still has over $1 million worth of crypto assets.
Credit: Source link